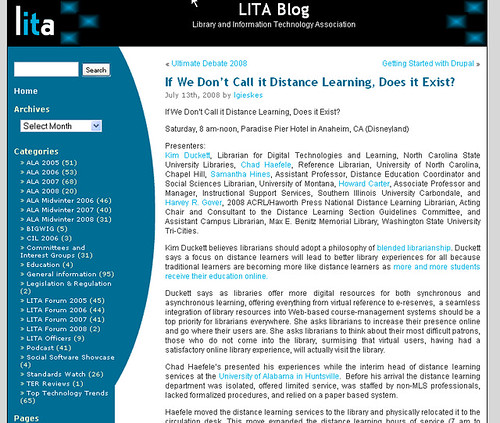
A really interesting spam hack popped onto my radar today. Here’s the post from the LITABlog, as seen in browser:
Here’s the bottom of the post. Nothing unusual, right?
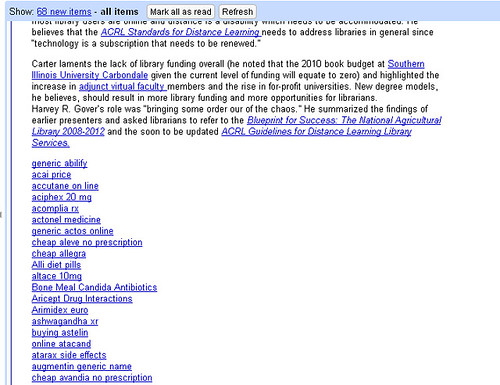
Here’s the same post in Google Reader:
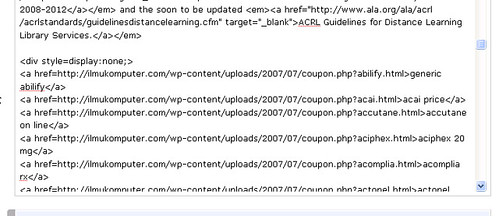
Spamolicious! Where the hell did all that come from? From this little piece of code in the post:
A hidden bit of code in the bottom of the post. I hadn’t seen this before, but Joshua M. Neff told me it happened to him as well. In the comments there was a link to the wordpress developer’s blog about a similar issue…but not an identical issue. I don’t think this is necessarily a SQL injection issue.
So: anyone have any thoughts? How did that code get put into an existing post? LITABlog is running the latest version of WordPress, so it’s not that. I don’t see any more of them, but I won’t unless I look through the code manually or whip up some SQL-fu that greps for the hidden css string. Which I will do if I must, but I thought maybe someone out there had a better idea. 🙂

6 replies on “Interesting WP Spam Hack”
SQL Injection would be my first guess, but its possible that a javascript attack could work as well. Untested, but I wonder if the permitted emphasis or bold tags could be exploited to make that happen.
I’d also check within the email or website fields. . .
More weirdness: when it happened to me, it didn’t show up in Bloglines but it did in Google Reader.
I removed the spam from the two posts on my blog and that seemed to solve the problem. Haven’t had it happen since.
this happened to the Library Student Journal blog which is hosted by LISHost. the wonderful Blake helped me out but it was too late – the blog was not salvageable. but maybe he knows how to fix it?
Did you ever see my post, Search Engine Marketeers are the new script kiddies? This is different though, in my case, my template got hacked.
Sounds like either an out of date WP with a xmlrpc vulnerability, or someone’s password got cracked. Another possibility is an evil plugin? Searching for similar posts would be easy, just look for
"display:none"Well…its not an out of date install. We’re current on that. It’s not a single password/user combo, because it was done on 5 different posts with 3 different users. Possibly a plugin…3 of the posts were podcasts, with associated plugin goodness.
I’ll keep digging. For now, everything is fixed.
SQL Injection would be my first guess, but its possible that a javascript attack could work as well. Untested, but I wonder if the permitted emphasis or bold tags could be exploited to make that happen.I'd also check within the email or website fields. . .